| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | 7 |
| 8 | 9 | 10 | 11 | 12 | 13 | 14 |
| 15 | 16 | 17 | 18 | 19 | 20 | 21 |
| 22 | 23 | 24 | 25 | 26 | 27 | 28 |
| 29 | 30 |
- 랜섬웨어
- 보안동향
- 코딩
- C language
- 리버싱 핵심원리
- Memory Forensics
- sql
- defcon.mem
- c언어
- 필기
- Defcon DFIR CTF 2019
- Code Up
- 실기
- 설치
- SQLD
- cmd
- codeup
- 오늘의 영어
- 다운로드
- 멀웨어
- 정처기
- 악성코드
- Volatility
- ctf
- 오늘의 보안
- 리버싱
- 보안
- C
- 정보보안기사
- 코드업
- Today
- Total
오브의 빛나는 별
[오늘의 보안] RustBucket와 KANDYKORN 혼합한 macOS 악성코드 본문
<3줄 요약>
- Discord를 통해 암호화폐 차익 거래 봇으로 위장한 악성 Python 애플리케이션을 다운로드하도록 하는 Cross-Platform Bridges.zip 배포
- Google 드라이브를 통해 악성코드 다운로드 후 HLOADER라는 Mach-O 페이로드를 다운로드하고 이름 변경
- AppleScript 애플릿과 'Internal PDF Viewer.app'이라는 Swift 기반 애플리케이션 번들 포함
RustBucket: 운영자가 명령 및 제어(C2) 서버와 통신하여 다양한 페이로드를 다운로드하고 실행
KANDYKORN: 가상화폐 거래 플랫폼의 블록체인 엔지니어를 대상으로 하며, 공격자들은 Discord 채널에서 가상화폐 커뮤니티의 멤버로 위장하여 Python 기반 모듈을 퍼뜨리는 방식
AppleScript 애플릿: 애플리케이션 작업을 지원하는 이미지, 템플릿 및 기타 파일과 같은 리소스. 스크립트를 애플리케이션 번들로 저장하면 번들 콘텐츠 서랍이 활성화되어 애플릿 번들 내의 리소스 폴더에 액세스할 수 있음
Swift 기반 애플리케이션: Apple이 iOS 및 Mac 앱 개발용으로 만든 프로그래밍 언어
https://thehackernews.com/2023/11/n-korean-hackers-mixing-and-matching.html
N. Korean Hackers 'Mixing' macOS Malware Tactics to Evade Detection
Lazarus Group's evolving cyber tactics target macOS systems by combining elements from multiple malware campaigns for better effectiveness and to avoi
thehackernews.com
The North Korean threat actors behind macOS malware strains such as RustBucket and KANDYKORN have been observed "mixing and matching" different elements of the two disparate attack chains, leveraging RustBucket droppers to deliver KANDYKORN.
The findings come from cybersecurity firm SentinelOne, which also tied a third macOS-specific malware called ObjCShellz to the RustBucket campaign.
RustBucket refers to an activity cluster linked to the Lazarus Group in which a backdoored version of a PDF reader app, dubbed SwiftLoader, is used as a conduit to load a next-stage malware written in Rust upon viewing a specially crafted lure document.

The KANDYKORN campaign, on the other hand, refers to a malicious cyber operation in which blockchain engineers of an unnamed crypto exchange platform were targeted via Discord to initiate a sophisticated multi-stage attack sequence that led to the deployment of the eponymous full-featured memory resident remote access trojan.
The third piece of the attack puzzle is ObjCShellz, which Jamf Threat Labs revealed earlier this month as a later-stage payload that acts as a remote shell that executes shell commands sent from the attacker server.
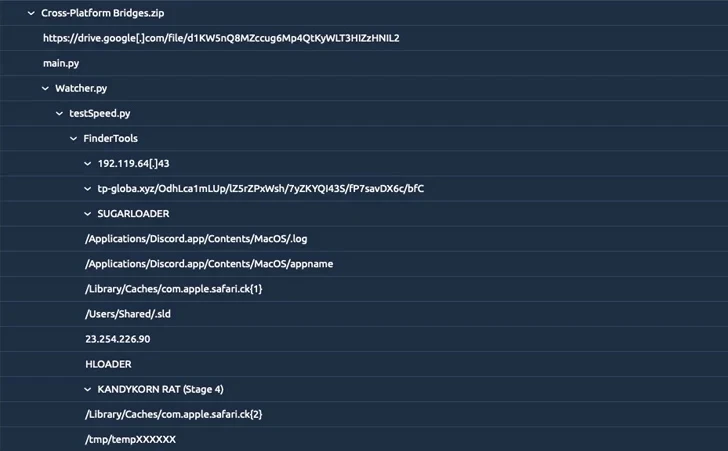
Further analysis of these campaigns by SentinelOne has now shown that the Lazarus Group is utilizing SwiftLoader to distribute KANDYKORN, corroborating a recent report from Google-owned Mandiant about how different hacker groups from North Korea are increasingly borrowing each other's tactics and tools.
"The DPRK's cyber landscape has evolved to a streamlined organization with shared tooling and targeting efforts," Mandiant noted. "This flexible approach to tasking makes it difficult for defenders to track, attribute, and thwart malicious activities, while enabling this now collaborative adversary to move stealthily with greater speed and adaptability."

This includes the use of new variants of the SwiftLoader stager that purports to be an executable named EdoneViewer but, in reality, contacts an actor-controlled domain to likely retrieve the KANDYKORN RAT based on overlaps in infrastructure and the tactics employed.
The disclosure comes as the AhnLab Security Emergency Response Center (ASEC) implicated Andariel – a subgroup within Lazarus – to cyber attacks exploiting a security flaw in Apache ActiveMQ (CVE-2023-46604, CVSS score: 10.0) to install NukeSped and TigerRAT backdoors.
'오늘의 보안' 카테고리의 다른 글
| [오늘의 보안동향] 사회복지자원봉사인증관리시스템(VMS) 개인정보 유출 의심사고 발생 (0) | 2024.01.15 |
|---|---|
| [오늘의 보안] Rust 기반 SysJoker 백도어 (0) | 2023.12.09 |
| [오늘의 보안동향] 급여이체확인증으로 위장하여 계정정보를 탈취하는 피싱 공격 (0) | 2023.12.02 |
| [오늘의 보안동향] 하남종합운동장 국민체육센터 홈페이지, 회원 6,658명 개인정보 유출 (0) | 2023.11.30 |
| [오늘의 보안동향] 익명의 방글라데시, 한국 정부부처 4곳에 DDoS 공격 주장 (0) | 2023.11.29 |


